Security researcher Charlie Miller, former NSA analyst now working for consultancy firm Accuvant, plans to publicly demonstrate a new security hole that could allow regular App Store apps to download and execute unsigned code on any iOS device. As Forbes reports, Miller, who isn’t new to the Mac and iOS hacking and security scene, plans to detail his discoveries at the SysCan conference in Taiwan next week.
Full details of the security hole aren’t available – Miller is apparently saving the presentation for next week to give Apple time to fix the issue, and the company is indeed already working on an iOS 5.0.1 update – but Miller had a “stealth app” approved by Apple in the App Store to record a video of the hidden “functionality”. The app was called Instastock, and it behaved as a regular stock monitoring app until Miller recorded a video of his iPhone being subject to malicious attacks through the app, which has since been pulled. Apparently, since Apple found out about Miller’s app and YouTube video, he’s also been removed from the iOS Developer Program.
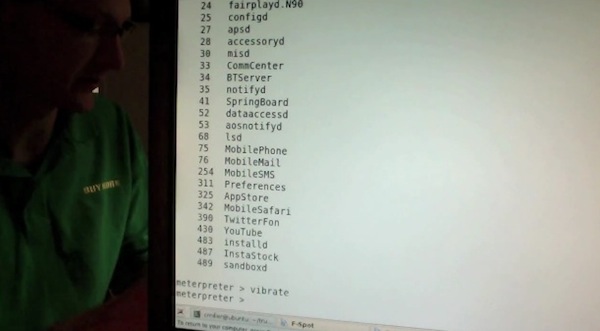
As you can see in the video, the app gets downloaded from the App Store as any other free or paid app. The first time Miller runs it on his iPhone, nothing happens and the app performs as advertised. But as soon as Miller activates the hidden functionalities on his web server, somehow connected to the iOS app, the app “phones home” and starts downloading and executing unsigned code. As per Apple’s technical rules and guidelines, App Store apps can only execute code approved by Apple. Yet with Instastock, Miller managed to make the iPhone vibrate remotely, open a YouTube video, and even download the device’s entire Address Book remotely. The app is seen exposing parts of the iOS filesystem, listing installed apps, and presumably giving access to a user’s documents, photos and more. In the video – which we’ve embedded below – you can also watch Miller execute commands remotely (from his computer to iPhone) using a command line interface.
Apparently, the hack has been made possible by a flaw in Apple’s JavaScript engine Nitro, introduced with iOS 4.3, that makes a series of system exceptions for Mobile Safari to render web pages faster. Forbes quotes Miller as saying “Apple runs all these checks to make sure only the browser can use the exception,” he says. “But in this one weird little corner case, it’s possible. And then you don’t have to worry about code-signing any more at all.”
Instastock has already been pulled from the App Store, and it’s unlikely that anyone else will figure out the exact bug that Miller has discovered before Apple releases iOS 5.0.1, which has reached beta 2 status and has been reported to introduce security fixes for iOS devices. Apple will likely include a fix for Miller’s discovery in iOS 5.0.1, but in the meantime you can check out the interesting demo after the break.