Last night JailbreakMe was released in the wild. As we reported, it’s one of the simplest jailbreak tools ever made, as it requires only one slide in Mobile Safari to install Cydia on your device. You visit a link, slide, and wait. As we also reported, though, the exploit seems to based on a PDF vulnerability in iOS: the iPhone automatically downloads PDF files, and Comex injected the jailbreak code in a PDF file.
Update #1: It’s not a PDF header issue, it’s the FlateDecode stream section.
Update #2: Charlie Miller says it’s not the FlateDecode stream section either (the bug Huang suggested it’s in Adobe’s renderer, not Apple’s), it’s a PDF font bug: [via DF]
“Starting to get a handle on jailbreakme.com exploit. Very beautiful work. Scary how it totally defeats Apple’s security architecture.”
Like I said, it’s pretty great for jailbreakers - but for “normal” people and Apple this is a serious threat to security.
So now that you’ve jailbroken your device, wouldn’t it be best to fix this hole, in order to prevent malicious softwares to land on your phone by using the same technique?
[Check out http://www.macstories.net/tag/jailbreak/ for our full Cydia / Jailbreak coverage]
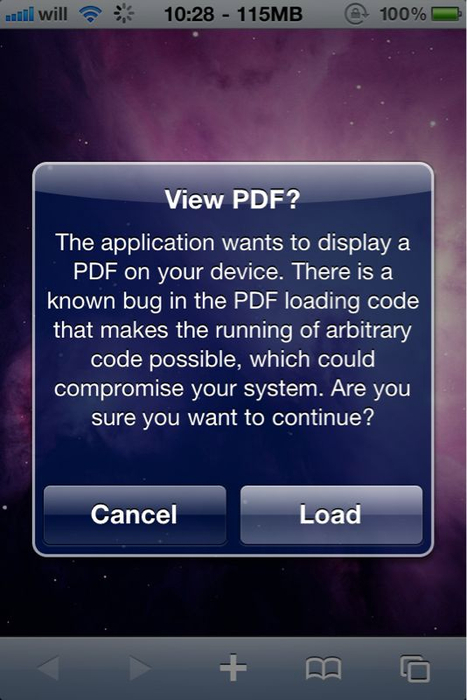
Tweeted by @cdevwill earlier today, all you have to do is download this .deb file and open it on your device using either Terminal from your Mac, or iFile on the iPhone. Just download it and place it in /var/mobile.
- Using Terminal:
ssh root@your IP address
alpine
dpkg -i file.deb
Where “alpine” is the default password you’ll get after installing Open SSH from Cydia and “your IP address” is located under Settings - > Wifi - > active wifi connection.
- Using iFile:
Navigate to /var/mobile and double tap on the .deb file to install it.
Please be aware that this won’t fix the issue, but it’ll simply ask you if you really want to open a .PDF every single time. If the source is trusted, you can confirm. But if you happen to visit a website that tries to install malicious stuff on your iPhone using @comex’s method, then you’ll be able to kill it.
Apple will surely address the bug in a future iOS release, but if you want to be safe right now - give it a try.