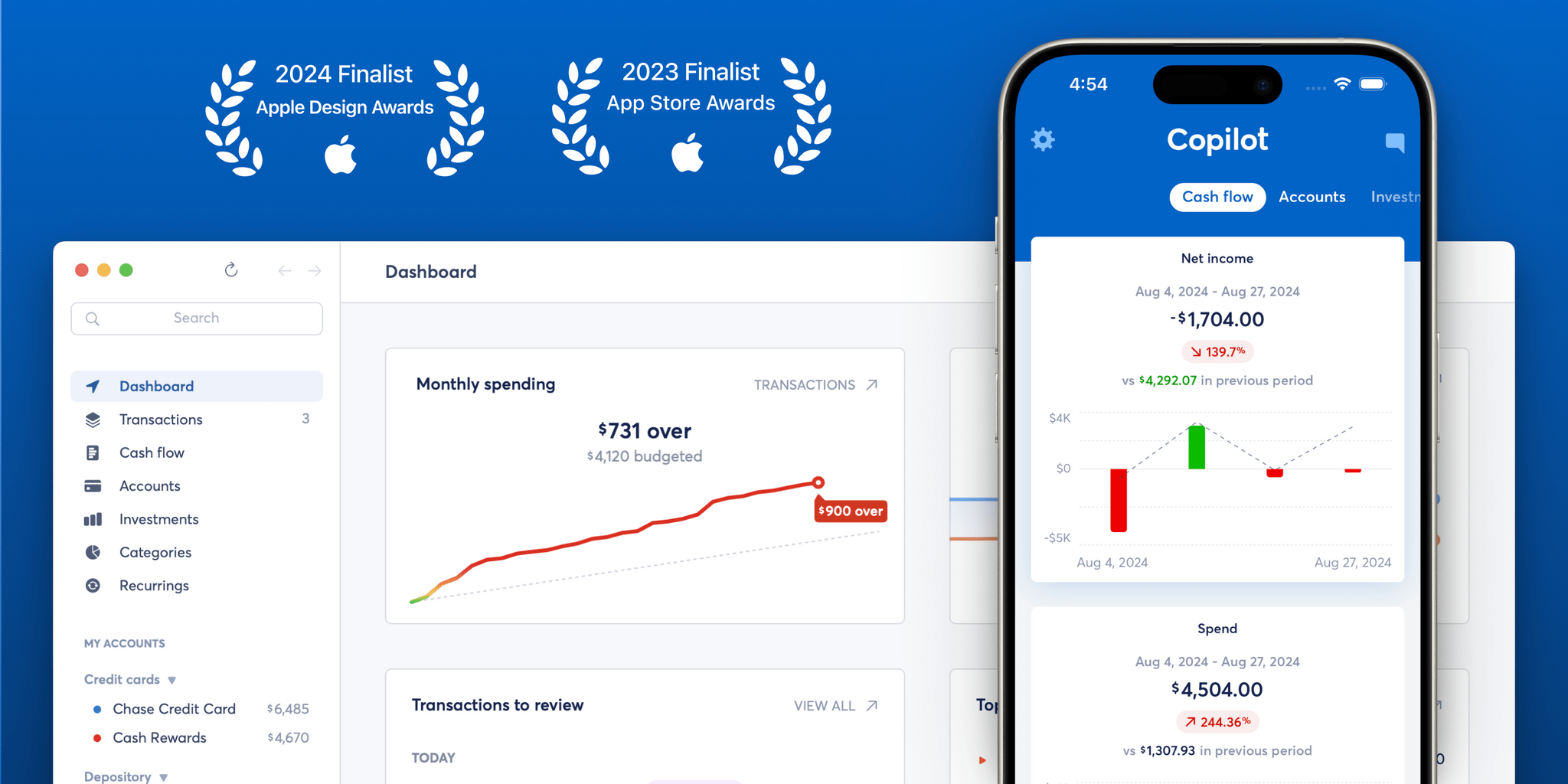
If you haven’t heard of Copilot yet, it’s time to check out Apple’s Editors Choice award-winning money tracker app. Copilot makes it simple to monitor your finances while providing valuable insights.
Their native iPhone and Mac apps can do it all: you can track your spending, budgets, investments, and net worth all in one place, allowing you to drill into the details without losing sight of the big picture.
In the Apple community, Copilot is known for staying in sync with new iOS launches, from responsive widgets to tinted icons ready for iOS18. Beyond beautiful design and functionality, Copilot’s mission is to build a future where everyone has a clear picture of their finances, without all the anxiety. Where anyone can reclaim their data from the banks to build their own plan for achieving their goals — with confidence and trust in their tools for doing so.
Copilot’s new Cash Flow section brings them closer to that vision. It focuses on three key areas: income, spending, and net income. You can easily compare your progress over different time frames to see how your financial habits stack up month-to-month or even week-to-week.
For a limited time, MacStories readers can get a special two-month free trial by using the code MACSTORIES when signing up. Visit their website to learn more and download Copilot from the App Store to get started today.
Our thanks to Copilot for sponsoring MacStories this week.