The September 2023 MGM hack quickly became one of the most notorious ransomware attacks in recent memory. Journalists and cybersecurity experts rushed to report on the broken slot machines, angry hotel guests, and the fateful phishing call to MGM’s help desk that started it all.
And, like a slick magic trick, the public’s attention was drawn in the wrong direction. Now, months later, we’re still missing something critical about the MGM hack.
That’s because, for many of the most important questions about the breach, the popular answers are either incomplete or inaccurate. Those include: who hacked MGM, what tactics they used to breach the system, and how security teams can protect themselves against similar attacks.
Why is that a problem? Because it lets us write off the MGM hack as a one-off story, instead of an example of an emerging style of attack that we’ll certainly be seeing more of. And that leaves companies and security teams unprepared.
Who hacked MGM?
Plenty of news stories have confidently blamed the MGM attack on either the Scattered Spider or ALPHV hacking group, but the truth is still murky, and likely involves a dangerous team up between different groups, each bringing their own expertise to the table.
Their attacks first use fluent English social engineering skills to get onto networks, where they then deploy sophisticated ransomware that quickly establishes persistence across multiple systems.
What tactics did they use?
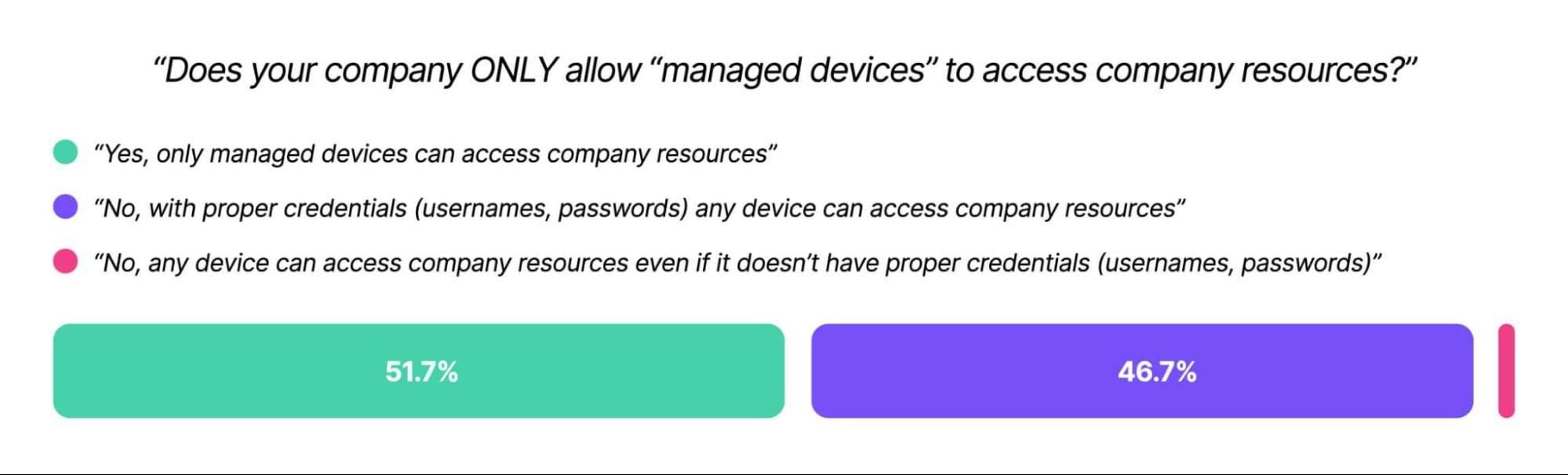
The dominant narrative has been that “a single phone call hacked MGM.” A phone vishing attack to MGM’s IT help desk is what started the hack, but there’s much more to it than that. The real issue is that this help desk worker was set up to fail by MGM’s weak ID verification protocols, and probably wasn’t doing anything “wrong” when they gave the bad actors access to a super administrator account.
How can security teams protect themselves?
Cybersecurity experts have centered most of their advice on user ID verification. But while it’s true that MGM’s help desk needed better ways of verifying employee identity, there’s another factor that should have stopped the hackers in their tracks.
That’s where you need to focus your attention. In fact, if you just focus your vision, you’ll find you’re already staring at the security story the pros have been missing.
It’s the device you’re reading this on.
To read more of what we learned when we researched the MGM hack–like how hacker groups get their names, the worrying gaps in MGM’s security, and why device trust is the real core of the story–check out the Kolide Blog.
Our thanks to Kolide for sponsoring MacStories this week.